Are you still using Windows 10? With Microsoft officially ending support on October 14, 2025, time is running out to upgrade to a supported operating system. But if your PC can’t handle Windows 11, don’t panic, there’s a safety net. Windows 10 Extended Security Updates (ESU) Program The Extended Security Updates (ESU) program is Microsoft’s […]
What Should You Do With a Lost USB Stick?
Why You Should Never Plug in a USB Stick You Found Finding a USB stick on the ground might feel like stumbling upon a mystery waiting to be solved, but before you plug it into your computer out of curiosity, stop. That small device could be hiding a big risk. The Hidden Dangers of Unknown […]
Thermal Paste Reminder
Replacing Thermal Paste in Your Computer: Why and How When was the last time you replaced the thermal paste in your computer? It’s crucial to monitor your computer’s temperature, especially during the summer, as excessive heat impairs its performance. Dust inside the casing is a common cause of overheating and cleaning it is a good […]
Overheating
Is your computer struggling with the heat? Overheating can cause a computer to slow down or even shut down entirely. Fortunately, there are several strategies you can employ to keep your computer cool, ranging from simple adjustments to more involved solutions. External Solutions Ensure Proper Airflow: One of the easiest ways to prevent overheating is […]
Phishing vs. Two-Factor Authentication
Recently, a friend shared that she received a phone call from someone claiming to be from her bank, requesting access codes from her authentication app. It turned out to be a scam aimed at gaining access to her bank account. Phishing Scams Phishing is a common scam where a malicious user tries to gain access […]
Location Sharing
For anyone venturing out alone, mobile phones can provide peace of mind. While being able to call someone in an emergency is invaluable, modern smartphones offer an extra layer of safety by allowing you to keep other people updated on your location in real time. It’s also more convenient sometimes to show someone where you […]
Windows 10 End of Life: Six Months Remaining
Are you still using Windows 10? The Clock is Ticking Windows 10 will reach its end of life in just six months. It will continue to receive updates until then, but official support will cease after that point. This might sound appealing if you’ve ever been interrupted by an untimely update, but the risks are […]
Why does the type of 365 licensing matter?
In our last article we talked about the history of the different account types. So, how much does this matter in a practical sense? It’s tempting to use a home licence for your business needs; it’s cheaper and business owners often already have a home licence that can be shared with up to five employees. […]
Personal and Work accounts; what’s the difference?
Click here for the previous article Following on from our previous article, where we summarised the basic differences between the account types, we realised that the amount we could say about it in detail is quite a lot. To avoid swamping users with a wall of text, we’re going to break it into smaller parts […]
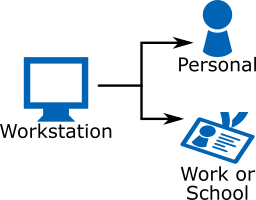
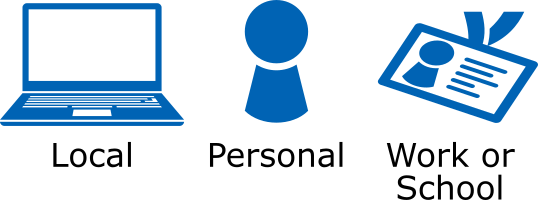
Types of Account
Do you know which kind of account you use to log in to your computer? There are three types and they each have different functionality. The local account belongs to the computer, the personal account belongs to an individual, and the work or school account belongs to an organisation. Here’s a quick explanation of what […]